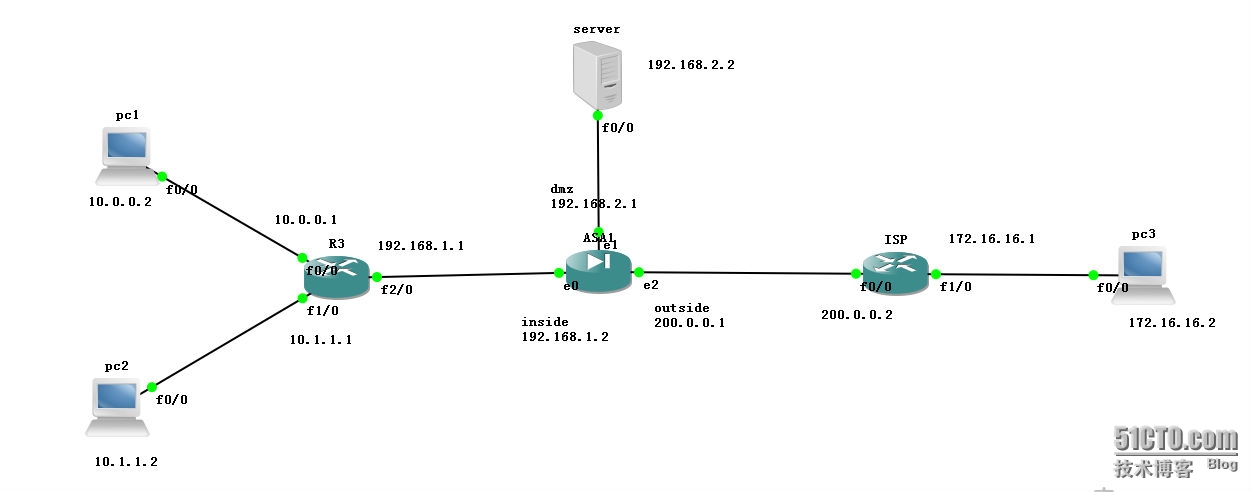
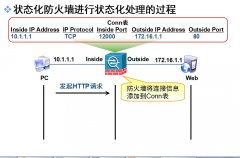
实验要求:
分别划分inside(内网),outside(外网),dmz(服务器区)三个区
配置PAT,直接使用outside接口的ip地址进行转换
配置静态NAT,发布内网服务器
启用NAT控制,配置NAT豁免,pc2访问outside区中的主机时,不做NAT转换
配置远程管理ASA,配置telnet,只允许pc2使用telnet接入
配置ssh,允许pc2和outside区ssh接入
在GNS3模拟器上配置如下:
一、接口和路由配置
1)asa配置
ciscoasa>
ciscoasa> en
Password:
ciscoasa# conf t
ciscoasa(config)# int e0/0
ciscoasa(config-if)# ip add 192.168.1.2 255.255.255.0
ciscoasa(config-if)# no sh
ciscoasa(config-if)# nameif inside
INFO: Security level for "inside" set to 100 by default.
ciscoasa(config-if)# int e0/1
ciscoasa(config-if)# ip add 192.168.2.1 255.255.255.0
ciscoasa(config-if)# no sh
ciscoasa(config-if)# nameif dmz
INFO: Security level for "dmz" set to 0 by default.
ciscoasa(config-if)# security-level 50
ciscoasa(config-if)# int e0/2
ciscoasa(config-if)# ip add 200.0.0.1 255.255.255.0
ciscoasa(config-if)# no sh
ciscoasa(config-if)# nameif outside
INFO: Security level for "outside" set to 0 by default.
ciscoasa(config)# enable password asa 设置特权密码
ciscoasa(config)# passwd asa 设置远程连接密码
ciscoasa(config-if)# sh int ip bri
Interface IP-Address OK? Method Status Protocol
Ethernet0/0 192.168.1.2 YES manual up up
Ethernet0/1 192.168.2.1 YES manual up up
Ethernet0/2 200.0.0.1 YES manual up up
Ethernet0/3 unassigned YES unset administratively down up
Ethernet0/4 unassigned YES unset administratively down up
Ethernet0/5 unassigned YES unset administratively down up
ciscoasa(config-if)# sh nameif
Interface Name Security
Ethernet0/0 inside 100
Ethernet0/1 dmz 50
Ethernet0/2 outside 0
ciscoasa(config)# route inside 0 0 192.168.1.1
ciscoasa(config)# route outside 172.16.16.0 255.255.255.0 200.0.0.2
ciscoasa(config)# sh route
Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default, U - per-user static route, o - ODR
P - periodic downloaded static route
Gateway of last resort is 192.168.1.1 to network 0.0.0.0
C 200.0.0.0 255.255.255.0 is directly connected, outside
S 172.16.16.0 255.255.255.0 [1/0] via 200.0.0.2, outside
C 192.168.1.0 255.255.255.0 is directly connected, inside
C 192.168.2.0 255.255.255.0 is directly connected, dmz
S* 0.0.0.0 0.0.0.0 [1/0] via 192.168.1.1, inside
2)R3配置
R3>en
R3#
R3#conf t
R3(config)#int f0/0
R3(config-if)#ip add 10.0.0.1 255.255.255.0
R3(config-if)#no sh
R3(config-if)#int f1/0
R3(config-if)#ip add 10.1.1.1 255.255.255.0
R3(config-if)#no sh
R3(config-if)#int f2/0
R3(config-if)#ip add 192.168.1.1 255.255.255.0
R3(config-if)#no sh
R3(config)# ip route 0.0.0.0 0.0.0.0 192.168.1.2
R3(config)#end
R3#sh ip int bri
Interface IP-Address OK? Method Status Protocol
FastEthernet0/0 10.0.0.1 YES manual up up
FastEthernet1/0 10.1.1.1 YES manual up up
FastEthernet2/0 192.168.1.1 YES manual up up
3)ISP配置
ISP(config)#int f0/0
ISP(config-if)#ip add 200.0.0.2 255.255.255.0
ISP(config-if)#no sh
ISP(config)#int f1/0
ISP(config-if)#ip add 172.16.16.1 255.255.255.0
ISP(config-if)#no sh
ISP(config)#ip route 0.0.0.0 0.0.0.0 200.0.0.1
4)pc配置
pc1(config)#int f0/0
pc1(config-if)#ip add 10.0.0.2 255.255.255.0
pc1(config-if)#no sh
pc1(config)#ip route 0.0.0.0 0.0.0.0 10.0.0.1 (在模拟器上有路由模拟的pc,这条是配置网关)
pc2(config)#int f0/0
pc2(config-if)#ip add 10.1.1.2 255.255.255.0
pc2(config-if)#no sh
pc2(config)#ip route 0.0.0.0 0.0.0.0 10.1.1.1
pc3(config)#int f0/0
pc3(config-if)#ip add 172.16.16.2 255.255.255.0
pc3(config-if)#no sh
pc3(config)#ip route 0.0.0.0 0.0.0.0 172.16.16.1
server(config)#int f0/0
server(config-if)#ip add 192.168.2.2 255.255.255.0
server(config-if)#no sh
server(config)#ip route 0.0.0.0 0.0.0.0 192.168.2.1
二、动态PAT配置
直接使用outside接口的ip地址进行转换
ciscoasa(config)# nat-control 启用NAT控制
ciscoasa(config)# nat (inside) 1 10.0.0.0 255.255.255.0 需要进行转换的网段
ciscoasa(config)# global (outside) 1 interface
或者
nat(inside)1 10.0.0.0 255.255.255.0
global(outside)1 200.0.0.1
这时pc2访问那台主机都已不行,因为启用NAT控制,pc2发起连接不匹配NAT规则,所以禁止出站。
pc2#telnet 172.16.16.2
Trying 172.16.16.2 ...
% Connection refused by remote host
配置豁免
ciscoasa(config)# nat (inside) 0 10.1.1.2 255.255.255.255
WARNING: IP address <10.1.1.2> and netmask <255.255.255.255> inconsistent
nat 0 10.1.1.0 will be identity translated for outbound
或者
asa(config)#access-list nonat permit ip host10.1.1.2 host 172.16.16.2
asa(config)nat (inside) 0 access-list nonat
pc2#telnet 172.16.16.2
Trying 172.16.16.2 ... Open
User Access Verification
Username:
这样就绕过了NAT规则。
ciscoasa(config)# sh xlate detail
2 in use, 3 most used
Flags: D - DNS, d - dump, I - identity, i - dynamic, n - no random,
r - portmap, s - static
TCP PAT from inside:10.0.0.2/11004 to outside:200.0.0.1/1024 flags ri
三、静态NAT(发布DMZ区的服务器)一对一的固定转换
ciscoasa(config)# static (dmz,outside) 200.0.0.5 192.168.2.2
ciscoasa(config)#access-list out_to_dmz permit ip host 172.16.16.2 host 200.0.0.5
ciscoasa(config)# access-group out_to_dmz in int outside
注意:acl配置命令中的目的地址应配置为映射地址200.0.0.5,而不是192.168.2.2
server(config)#ip http server 启动http
pc3#telnet 200.0.0.5 80
Trying 200.0.0.5, 80 ... Open
ciscoasa(config)# sh xlate detail 查看NAT转换表
3 in use, 3 most used
Flags: D - DNS, d - dump, I - identity, i - dynamic, n - no random,
r - portmap, s - static
NAT from dmz:192.168.2.2 to outside:200.0.0.5 flags s
四、远程管理ASA
1)配置允许telnet接入
ciscoasa(config)# username lijun password 123456
ciscoasa(config)# aaa authentication telnet console LOCAL
ciscoasa(config)# telnet 10.1.1.2 255.255.255.255 inside
只有pc2能telnet ASA防火墙
pc2#telnet 192.168.1.2
Trying 192.168.1.2 ... Open
User Access Verification
Username: lijun
Password: ******
Type help or '?' for a list of available commands.
ciscoasa>
pc1#telnet 192.168.1.2
Trying 192.168.1.2 ...
% Connection timed out; remote host not responding
pc1 是不能连接
2)配置ssh接入
ciscoasa(config)# host asa 配置主机名
asa(config)# username lihao password 123456
asa(config)# aaa authentication ssh console LOCAL
asa(config)# domain-name benet.com 配置域名
asa(config)# crypto key generate rsa modulus 1024 生成RSA密钥对
INFO: The name for the keys will be: <Default-RSA-Key>
Keypair generation process begin. Please wait...
asa(config)# ssh 10.1.1.2 255.255.255.255 inside 允许pc2 连接防火墙
asa(config)# ssh 0 0 outside 允许外部连接ASA 防火墙
pc2#SSH -L lihao 192.168.1.2
Password:
Type help or '?' for a list of available commands.
asa>
内部只有pc2可以使用ssh接入,外部任何主机
pc3#ssh -l lihao 200.0.0.1
Password:
Type help or '?' for a list of available commands.
asa>
(额外补充)端口映射命令
static (dmz,outside) tcp 200.0.0.5 80 192.168.2.2 80
access-list out_to_dmz permit ip host 172.16.2.2 host 200.0.0.5
access-group out_to_dmz in int outside
五、查询命令
sh nameif 查询区域
sh int ip bri 查询ip配置
sh ssh 查看ssh配置信息
sh crypto key mypubkey rsa 查看产生的rsa密钥值
crypto key zeroize
asa(config)# capture telnet interface outside 抓包排错
ASA(config)# no capture telnet 关闭抓包
asa(config)# sh capture ssh
119 packets captured
1: 02:36:50.108057 172.16.16.2.11005 > 200.0.0.1.22: P 710551790:710551842(52) ack 856118752 win 3644
2: 02:36:50.108057 200.0.0.1.22 > 172.16.16.2.11005: . ack 710551842 win 8192
3: 02:36:50.108041 200.0.0.1.22 > 172.16.16.2.11005: P 856118752:856118804(52) ack 710551842 win 8192
4: 02:36:50.139809 172.16.16.2.11005 > 200.0.0.1.22: . ack 856118804 win 4128
5: 02:36:51.418099 172.16.16.2.11005 > 200.0.0.1.22: P 710551842:710551894(52) ack 856118804 win 4128
6: 02:36:51.418099 200.0.0.1.22 > 172.16.16.2.11005: . ack 710551894 win 8192
7: 02:36:51.418099 200.0.0.1.22 > 172.16.16.2.11005: P 856118804:856118856(52) ack 710551894 win 8192
8: 02:36:51.680583 172.16.16.2.11005 > 200.0.0.1.22: . ack 856118856 win 4076
9: 02:36:52.698755 172.16.16.2.11005 > 200.0.0.1.22: P 710551894:710551946(52) ack 856118856 win 4076
10: 02:36:52.698755 200.0.0.1.22 > 172.16.16.2.11005: . ack 710551946 win 8192