一.参考链接:
----按如下链接可以配置,在redhat linux可以实现目标地址为哪个块网卡地址,就从哪块网卡回去:
http://bbs.chinaunix.net/thread-3661955-2-1.html[^]
----实际测试,即使不做任何配置,只配置一个默认网关,虽然icmp,tcp的流量从管理口进入,从业务口返回,也是没有问题的,可以正常接收ICMP和TCP会话建立(对于交换式的UDP不方便测试,没有测试)
二.测试环境:
/ (eth0)PC2
PC1(eth0)------------router\(eth1)PC2
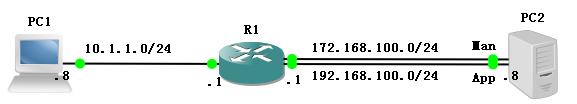
A.PC1 :
----windows xp
eth0:10.1.1.8/24 默认网关:10.1.1.1(路由器地址)
B.router
e0/0:10.1.1.1/24
e0/1:172.16.100.1/24
e0/2:192.168.100.1/24
C.PC2:
----Linux AS4 2.6.9-78.EL0000001Wed Jul 9 15:27:01 EDT 2008 i686 i686 i386 GNU/Linux
eth0:172.16.100.8/24 没有设置默认网关,规划走管理流量
eth1:192.168.100.8/24 默认网关:192.168.100.1,规划走业务流量
三.配置步骤:
A.添加路由表:
#vi /etc/iproute2/rt_tables
251 APP
252 MAN
B.两个路由表设置不同的默认路由:
ip route add default via 172.16.100.1 dev eth0 table APP
ip route add default via 192.168.100.1 dev eth1 table MAN
C.两个路由表设置策略路由:
ip rule add from 172.16.100.8 table APP
ip rule add from 182.168100.8 table MAN
----注意:这个地方是rule,不是route
D.将上述语句写到开机脚本中:
# vi /etc/rc.local
ip route add default via 172.16.100.1 dev eth0 table APP
ip route add default via 192.168.100.1 dev eth1 table MAN
ip rule add from 172.16.100.8 table APP
ip rule add from 182.168100.8 table MAN
四.效果测试:
A.配置前,用PC1去ping PC2的管理口地址时,回包是从业务口回的
-----因为只有业务口配置了默认路由
[root@AS4 ~]# tcpdump -i eth0 icmp
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 96 bytes
11:00:40.672269 IP 10.1.1.8 > 172.16.100.8: icmp 40: echo request seq 26368
11:00:41.714285 IP 10.1.1.8 > 172.16.100.8: icmp 40: echo request seq 26624
11:00:42.715187 IP 10.1.1.8 > 172.16.100.8: icmp 40: echo request seq 26880
11:00:43.714274 IP 10.1.1.8 > 172.16.100.8: icmp 40: echo request seq 27136
B.配置后,用PC1去ping PC2的管理口地址时,回包也从管理口回的
----因为配置了策略路由,从管理口发出的包,走MAN路由表,而MAN路由表配置的默认路由为管理口对端的地址
[root@AS4 ~]# tcpdump -i eth0 icmp
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 96 bytes
11:05:42.460413 IP 10.1.1.8 > 172.16.100.8: icmp 40: echo request seq 27392
11:05:42.483457 IP 172.16.100.8 > 10.1.1.8: icmp 40: echo reply seq 27392
11:05:43.454196 IP 10.1.1.8 > 172.16.100.8: icmp 40: echo request seq 27648
11:05:43.454250 IP 172.16.100.8 > 10.1.1.8: icmp 40: echo reply seq 27648
11:05:44.462939 IP 10.1.1.8 > 172.16.100.8: icmp 40: echo request seq 27904
11:05:44.462996 IP 172.16.100.8 > 10.1.1.8: icmp 40: echo reply seq 27904
11:05:45.457045 IP 10.1.1.8 > 172.16.100.8: icmp 40: echo request seq 28160
11:05:45.457555 IP 172.16.100.8 > 10.1.1.8: icmp 40: echo reply seq 28160